It seems common to see our data to be compromised by viruses, which come from certain unknown files or causal clicks. However, the era of telephones and computers has brought many untested applications, which access all our data in a very easy way. And it’s not just photos and a phone book.
We are connected to social networks, we use emails, banking services, GPS coordinates, and much more. Practically, our lives are on our devices. Therein lies the answer to why you need some of the data protection applications.
How many times have you installed an application and only accepted everything it requires, without reading? This is exactly what can compromise your data. They often require access to a phonebook or camera. If they are unverified, your data can easily fall into the hands of hackers.
When you use a free Wi-Fi network, you probably have no idea that data can be misused even if there are specific recipients of thee shared data. The same thing happens if you charge your phone on an unknown computer. It may not be visible, but data can be transmitted.
Related: What is BitLocker and What Does it do?
Password manager as a path to security
Passwords have become a basic necessity when using a computer or phone. Passwords provide a basic level of security to protect our personal or business information. Yet most of us have a hard time remembering them and use simple passwords.
Why do we need passwords? Passwords are there to protect some of our most important personal information.
Think of a password as an online key. In the physical world, we use different keys for each lock. There are different keys for the house, car, garage, office, bicycles.
Our online world is no different. Companies provide locks and we have to provide the keys.
In the physical world, we would never use just one key, but online more than half of us use the same, simple password. For some of our greatest private and personal aspects of our lives, most of us use the same key. The most common and insecure passwords are: “123456”, “password”, “qwerty”, “abc123”, date of birth, name of someone in the family, phone number, etc.
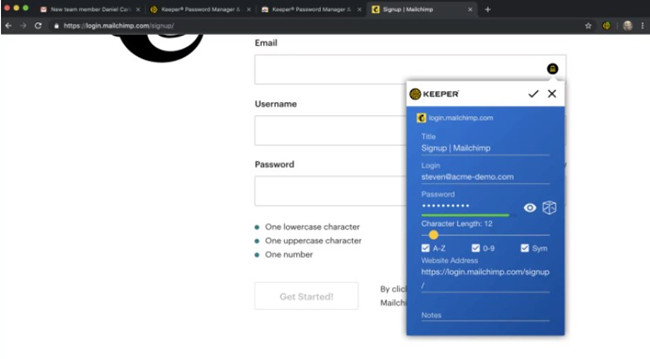
Creating a strong password is extremely important to keep your data secure. The tool that you can use to form a stronger password is Keeper Password Manager. This security solution software comes with features that provide your chat services an encrypted layer of security and store your passwords in a cloud-based vault. Creating a password with a minimum of 9 characters is ideal. The combination of lowercase and uppercase letters, numbers, signs is the most suitable and most recommended. Codes must be created so that they are easy to remember. One way to do this is to create a code based on the title of a favorite song, affirmation, or other phrases.
Common passwords – Common passwords are often provided by the product manufacturer. It is important to change the password during the first setup process, or if you have ever reset to factory settings. Without changing the password, the device becomes vulnerable and susceptible to hacking. Password management tools – As you know, all these different passwords are impossible to remember without password security tools.
Password management tools are tools that will store and organize passwords for you. These tools will keep all your passwords secure and encrypt information. Depending on your password management tool, passwords will be stored on your computer or Claud. There are several different password management tools. Some provide space for passwords, others organize them, while some randomly generate them for you.
Two levels of authentication – When you are satisfied that you have a secure password, consider providing a double level of authentication. Many popular websites hosted on servers use dual-level authentication as an additional level of security. Two-level authentication is a simple function that requires more than a password, and it is often used to re-confirm who you are. It requires both something “you know” (like a password) and something “you have” (like a cell phone).
After entering the password, the password will be sent to you, usually via a mobile phone. You will be asked to enter a password code to access your account. Security token password management tools will provide two levels of authentication for each website that requires logging in. They usually take the form of a USB key or token. They create code with a random combination of characters that you use to log in to the website. The idea of a security token password management tool is to create a second layer of protection.
Don’t forget – All information shared or online is subject to a breach of confidentiality, availability, or integrity. Change the default password. Use a different password for each service. If you can’t remember all your passwords, use tools such as password management tools or two levels of authentication can be of great help. And change your password regularly. Uses strong passwords, with a minimum of 12 characters.
Precaution is the best defense
At a time of increasingly sophisticated cyber attacks that threaten to cause disastrous losses in business, the first protection measure is the secure management of user accounts and passwords. To apply them effectively, you also need to know how hackers think, and what is the sequence of the most important steps in defending against cyber abuse.
Cyber attacks can be motivated by various reasons, but each of them necessarily implies to download the user account of one of the users on the system, through which they will get access to certain company resources. At the same time, the greater the authority of the stolen account is, the greater the possibilities of the cyber attack.
A user account can be misused in several ways, depending on the techniques used by the cyber attacker. In some cases, these are social engineering attacks, when an attacker tries to deceive the company’s employees to get a username and password to access the information system. In other cases, various techniques of cracking user passwords with different tools made for this purpose are used.
More Articles:
4 Ways to Reset the Forgotten Password on Windows 10
What is Syskey and Why is it not Supported Now on Windows 10?